Introduction
ChromeSetup.exe is not a real Chrome installer it’s malware.
It hides behind a familiar name to steal personal data like passwords
cookies and crypto wallets.
File Details
File name: ChromeSetup (1).exe
Hash Signature –
MD5: 7c89b48a2752a771eb6457fe2fea1d8e
SHA1: afb602ef798b23f400fd3d474cb570aa781797c4
SHA256: 3d1e16dec7f88b3ccdf7197c64a6eea6a7d3599c12f34893d60012ffd61f15ce
File Type: Win32 EXE
File Size : 1.41 MB (1482240 bytes)
What does he do?
❑ Executes multiple trusted system processes
❑ Blends in with regular Windows behavior
❑ Uses a suspicious command
File Paths (IOC)
• C:\Users\Lab\AppData\Local\Temp\tmp7FE8.tmp
• C:\Users\Lab\Desktop\SPW AW25 – PO.010 SMS.exe
• C:\Users\Lab\AppData\Local\Temp\tmp4BC8.tm
• C:\Users\Lab\AppData\Local\Temp\tmp4BC8.tmp
• C:\Users\Lab\AppData\Local\Temp\tmp7FE8.tmp
• C:\Users\Lab\AppData\Local\Temp\tmp5406.tmp
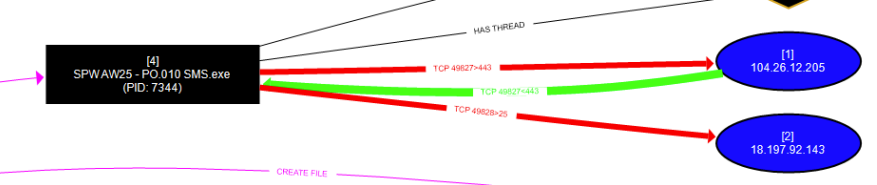
Network Connections Malware contacted
104.26.12.205
18.197.92.143
• Command and Control
• Sending stolen data
• Downloading more payloads
Registry Keys
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Notifications\Data\418A073AA3BC3475
HKLM\SYSTEM\WaaS\WaaSMedic\TaskStore\Schedule Work
HKLM\SYSTEM\WaaS\WaaSMedic\TaskStore\Schedule Maintenance Work
- Tricks the system into thinking dangerous websites are safe
- Helps bypass internet protection
- Hides inside the Windows notifications system
- Makes it harder to detect
- Uses Windows maintenance tasks to keep running
- Stays active even after reboot
ChromeSetup Summary
Looks like a normal file
The file name seems like a document: SPW AW25 – PO.010 SMS.exe
Creates secret files
It makes temporary files with strange names
like: tmp7FE8.tmp, tmp5406.tmp
Network Activity – In Simple Words
After it runs, the malware tries to connect to
the internet It contacts these two suspicious
IP addresses: 104.26.12.205 18.197.92.143
Detection rolles
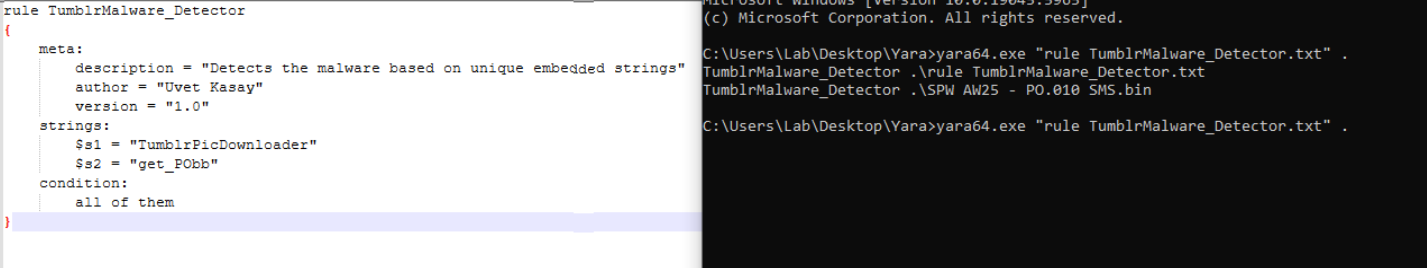
What This YARA Rule Does
This rule helps find the malware by looking inside files for two rare strings
TumblrPicDownloader – the name of the hidden program get_
PObb – a strange function used by the malware